
Starting from the “major issue” of protecting voice of protagonists questioned in reports and interviews, particularly in criminal matters, the company Swealink has developed Vox Protect, software guaranteeing the protection of witnesses, according to a press release from its President Christophe Henrotte. The result of four years of work led by this sound engineer, with several researchers, and supported by Riam, CNC, BPI and Inriq, this solution uses a random algorithm and, through its mode of operation, makes it possible to “protect both the voice of the witness, the user (the technician), and the software itself, in particular thanks to an anti-piracy key”, it is stated.
Until now, one of the means of protecting witnesses consists of modifying their voice by ” linear effects ” like the “pitch effect ” which consists of a “transformation of the tone of a processed signal” without however degrading the sound, it is said. Practically, this effect does not modify “in any way” the fundamentals of the sound signal. The method dating from the “analog era” thus appears outdated at a time when “simple inverse functions”, accessible on the Internet, help to make all existing audio effects reversible and, therefore, no longer guarantee the anonymity of witnesses.
A finding confirmed by the Cnil which notes, in an article of January 4, that the technique of “pitch shifting” provides “ extremely weak protection “in the light of the new sound software available on the market. “This technique could be of interest when reverse engineering costs were high and accessible only fo a limited number of people a few decades ago, which is no longer the case with the transition to digital technology and software accessibility”, it concludes.

LE LOGICIEL VOX PROTECT :
COMMENT PROTEGER VERI TABLEMENT LA VOIX DES TEMOINS ?
Notre voix est l’un de nos ” biens ” les plus précieux. Mals c’est aussi une donnée, un moyen de reconnaissance qu’il nous faut protéger. Le logiciel Vox Protect développé par Christophe Henrotte, directeur de studio MAIA vise justement à renforcer la protection des témoins. Retour sur les enjeux autour de cette innovation.
Témoignages télévisés, conversations privées, appels téléphoniques, notes vocales … toutes ces situations, pour la plupart quotidiennes, peuvent être exploitées à notre insu.
Parce que oui, aujourd’hui, il est possible de reconnaître l’identité, l’âge, le sexe, l’état de santé d’une personne grâce à sa signature vocale.
La protéger est donc un enjeu majeur de notre société.
UN RISQUE DE CINQ ANS D’EMPRISONNEMENT
D’ailleurs, le Règlement général sur la protection de données (RGPD), protège justement, à l’article 4¹ « la data personnelle», dont fait partie notre voix.
Comme le droit à l’image d’une personne, le« droit à sa voix » fait partie, depuis un procès de 1982, de ce qu’on appelle en France « les droits de la personnalité», explique l’article² de la Commission nationale de l’informatique et des libertés (CNIL). La CNIL a d’ailleurs rappelé dans un article³ publié le 4 janvier 2022, que la non ou mauvaise protection d’un témoin est
« punie de 5 ans de prison et de 75 000€ d’amende ». Ainsi établie comme une donnée juridiquement et légalement protégée, le témoignage anonyme d’une personne doit rester anonyme, doit rester irréversible.
LE PITCH:
LA FAUSSE PROTECTION
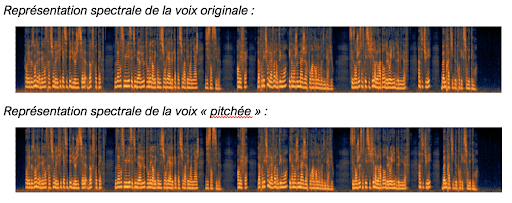
Protéger et garantir l’anonymat de la voix des témoins se doit donc d’être une priorité. Mais les nombreux effets linéaires, comme le pitch très majoritairement utilisé par les professionnels du son, ne protègent en rien les témoins, leur voix étant facilement retraçable. L’effet utilisé de pitch est « une mesure de protection extrêmement faible », assure la CNIL. « il n’est pas compliqué techniquement de modifier {la voix} dans le sens inverse pour se rapprocher rapidement de la voix réelle et ainsi pouvoir ré-identifier la personne». En prenant l’exemple de représentation spectrale ci-dessous, l’analyse avant et après du pitch montre que le signal n’a pas été modifié, puisqu’il n’y a aucune différence sur les harmoniques du signal.
L’année 2013, en France, a prouvé à quel point il était facile d’identifier la signature vocale d’un individu, avec comme simples outils un enregistrement et un logiciel de reconnaissance vocale. C’est l’affaire« Cahuzac », mettant en cause l’ex-ministre du Budget, qui met en avant ce risque.
Le fameux enregistrement téléphonique, instrument de sa chute, dévoilé par Mediapart, a été nettoyé par les experts du Service central de l’informatique et des traces technologiques (SCITT), puis convertie en courbes afin d’établir une signature vocale. Ensuite, entre en jeu le logiciel Batvox, qui a permis de comparer l’enregistrement à des discours de l’ancien ministre Jérôme Cahuzac, et d’établir un degré de ressemblance. Aucun doute, donc, sur la possibilité de reconnaître l’identité d’une personne grâce à sa voix.
Cependant, le risque est largement plus important pour les personnes témoignant dans des affaires dites «sensibles» ou souhaitant conserver leur anonymat pour leur sécurité.
En clair, une voix de témoin pitchée peut être facilement identifiable en inversant le processus.
La voix des témoins n’est pas protégée.
1.https://www.servicesmobiles.fr/la-voix-est-une-donnee-personnelle-sensible-que-dit-le-rgpd-45787
2. https://linc.cnil.fr/fr/les-droits-de-la-voix-12-quelle-ecoute-pour-nos-systemes
3. https://linc.cnil.fr/protection-des-temoins-casser-la-voix-et-limage
VOX PROTECT:
UNE SOLUTION POUR GARANTIR L’ANONYMAT DES TÉMOINS
Nous avons travaillé plus de quatre ans avec des chercheurs du CNRS et de l’INRIA pour développer un plug-in qui garantit la protection de la voix des témoins. Ces travaux étant concluants, nous avons créé la société Swealink et développé le produit Vox Protect afin de le commercialiser.
Nous avions envisagé plusieurs pistes de réflexion, notamment la resynthèse vocale, qui est l’une des pistes couramment envisagées de nos jours.
Le principe de la resynthèse vocale est assez simple. D’une part, on récupère le texte dit par le témoin par une brique de Speach2text et, d’autre part, on analyse la prosodie de la voix afin d’en conserver les émotions. Le texte et les informations de prosodies sont alors analysés et on reconstitue la nouvelle voix à partir d’un corpus distinct de voix existante.
Cette approche pré- sente plusieurs inconvénients, dont certains sont rédhibitoires dans le cas qui nous occupe, où l’on cherche que la voix du témoin soit protégée, mais également entendue par un spectateur (lors d’un journal télévisé ou sur un documentaire).
Pour reconstituer l’émotion de la voix initiale, il est nécessaire de réunir un corpus très important, avec plusieurs gigaoctets de voix disponibles.
Ce corpus est également sensible à la langue, en fonction de l’accent de l’ancienne ou de la nouvelle voix. Il est donc probable qu’il faille stocker ce corpus en dehors de la machine de l’ordinateur sur lequel est fait le traitement, d’une part, et/ou qu’il faille envoyer les informations: voix originale, texte original, dans le cloud pour un traitement distant, ce qui crée une faille de sécurité. La puissance nécessaire pour faire fonctionner un tel process en temps réel impose des ressources machines également très importantes, parfois incompatibles avec ce qu’autorisent les outils de montages sons sur lesquels serait branché le plug-in. Une quête de performance viendrait à simplifier la prosodie, voire à créer des erreurs d’interprétation, ce qui pose des questions sur le plan déontologique.
Par ailleurs, dans un contexte sensible de protection d’un témoin, nous pourrions rencontrer des limites en termes de droits d’auteurs et de droit moral du comédien qui a enregistré le corpus de. A-t-il donné son autorisation pour que sa voix soit utilisée pour évoquer une attaque terroriste ?
Pour l’ensemble de ces raisons, nous avons cherché à concilier une approche plus classique, mais avec une originalité dans le traitement aléatoire qui rend la transformation indétectable.
Nous avons donc retenu l’option d’un traitement par modulation aléatoire qui permet de travailler en temps réel. Il s’agit de faire subir au signal trois variations indépendantes les unes des autres. Ces variations fonctionnent sur un temps très court, de moins d’une seconde et rendent impossible la réversibilité. Par ailleurs, le logiciel ne gardant aucune trace, la protection du témoin est ainsi assurée : si on passe la même voix deux fois à travers ce processus de transformation, la voix transformée sera donc différente.
Comme il s’agit d’une adjonction de transformations linéaires, on conserve la prosodie et donc l’émotion du témoignage.
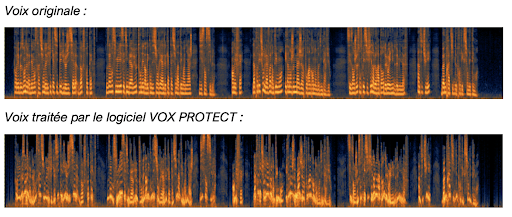
Si on reprend la comparaison entre la voix originale et la voix traitée, nous constatons que le signal a bel et bien subi des transformations importantes, protégeant donc le témoin d’une reconnaissance vocale par analogie des signaux.
DES NIVEAUX DE PROTECTION ADAPTÉS AUX BESOINS

Deux niveaux de protection ont été mis en place pour s’adapter au mieux au besoin de chaque témoin.
Le premier est le « Low Level of Protection » qui correspond à un niveau bas de protection, soit un témoignage sur des affaires courantes sans risque majeur autre que la réversibilité du processus : il protège d’une réversion effectuée par un pitch.
On peut le renforcer par une légère variation des modulations. En revanche, ce niveau ne protègera pas d’une attaque par des services « spécialisés » qui ont accès à des outils beaucoup plus perfectionnés comme la reconnaissance vocale assistée par ordinateur.
Le second, le « High Level of Protection », permet, comme son nom l’indique, d’atteindre un niveau de protection plus important. Il est donc conseillé pour des cas comme le témoignage dans une affaire terroriste.
En revanche, ce niveau nécessite un ajustement pour trouver le meilleur compromis entre protection et lisibilité du message.
Nous avons la volonté de proposer des améliorations au fil de l’eau par des mises à jour régulières et des changements de versions, a priori tous les deux ans.
N’hésitez pas à nous contacter si vous souhaitez plus d’informations. Les premiers retours seront in- dispensables pour nous assurer que cet outil remplit parfaitement sa vocation.
Christophe Henrotte


Witness protection: cracking the voice and image
Written by Martin Biéri & Alexis Léautier
Translated by VoxProtect
–
04 january 2023
The issue of witness protection is not recent: there are legal measures to protect the anonymity of witnesses, especially when there is a risk of endangering their integrity (or that of their relatives). However, the technical measures that are supposed to guarantee this anonymity through the modification of audio and video information have certain limits, which are constantly being pushed back by technological progress.
The protection of the witness’s identity
While whistleblower protection has been strengthened with the Waserman Act in 2022 and the transposition of the European Directive in 2019, the question of anonymity protection in legal or journalistic contexts remains an issue, especially in light of technological advances.
While measures to protect witnesses have been in place in France for several years – to protect them from external influence, such as witness subordination or other means of pressure, but also in use, such as protecting the identity of police “informers” in official reports – they have been strengthened since 2001, allowing for the organization of the legal structure of anonymous testimony, “an important novelty inspired by the accusatory procedures of common law countries” (Citoyens et délateurs, 2005).
Thus, it contains new measures that provide a way to conceal certain information that presents a risk for witnesses. For example, witnesses can give the address of the police station rather than their own to avoid reprisals from the person they are incriminating.
This reinforcement continued in 2016, bringing out some technical clarifications in particular. Indeed, in legal proceedings (in the case of a felony or misdemeanor punishable by at least three years in prison), the witness may be required to appear, with measures to protect him or her from being re-identified: “In certain circumstances (for example, if his or her safety is no longer assured), the witness may be allowed to use an assumed name. If confronted with the suspect, the confrontation will be conducted remotely. The witness will not be visible and his/her voice will be masked. The revelation of the identity or address is punishable by 5 years in prison and a fine of 75,000 €” (service-public). These new additions are to be understood in the context of the fight against terrorism, and particularly following the attacks of 2015, as indicated in the title of the text.
Thus, in addition to keeping the individual’s identity (name, surname, address, etc.) secret, i.e. keeping it outside or beside the procedure, there are two ways to protect him: by “removing” his image (being visible) and by “masking” his voice. In the first case, not being present (” remotely “) is a simple and obvious measure: the physical absence of the individual from the court room (for example, in the confrontation) obviously protects him. Then there are other measures to degrade the image so that it does not provide any direct identification information (blurring or pixelation for example).
Regarding the voice, the technical measures used are also quite well known: it is generally about modifying the voice, by shifting it towards the high or low frequencies. It is not a question here of a degradation of the sound, but of a transposition, what is called “pitch shifting” (see also below).
These techniques can also be found in the context of television reports, in which people testify in exchange for protection of their anonymity, on more or less sensitive subjects. Several devices exist: the person can be off-camera or in the shadows, which makes it possible to have only a vague silhouette; the person can be “blurred” (a filter is added over the image or, on the contrary, the quality of the image is degraded to a greater or lesser degree in order to mask what is considered to be the most identifiable, that is, the face); the person can be anonymized by a black blindfold; he or she can also be replaced by an actor or journalist reading his or her words – or his or her words can be simply written on a card.
Inherent limitations to the technique
The voice
But are these technical measures truly sufficient? First of all, in the case of voice, it is not technically complicated to modify the voice in the opposite direction in order to quickly get closer to the real voice and thus be able to re-identify the person. This operation is available in most sound editing, recording or music creation software, including free ones. “Pitch shifting”, this famous linear modulation of the signal, seems to be an extremely weak protection measure in the context of witness protection or source protection. This technique could have been interesting when the costs of reverse engineering were important and accessible only to a limited number of people a few decades ago, which is no longer the case with the passage to the digital format and the accessibility of software.
Moreover, the voice is a variable geometry data (see the White Paper on voice assistants and our articles The rights of the voice): in addition to being a characteristic specific to everyone, it is the vehicle of the transmitted message. The way of speaking, the language tics, the accent… are all clues to be able to identify the person. And, by extension, we find all the classic issues related to data anonymization: removing directly identifying attributes is not necessarily sufficient. It is possible to re-identify a person (by inference or cross-checking) thanks to the contextual information provided in the record.
The most famous example of these loopholes is the re-identification of Sonia (who is an alias). This person who had provided information about a terrorist and helped prevent an attack in 2015 had her identity revealed. As a result, she was forced to change her name, address, etc. This incident had also led to the bill “Fight against organized crime, terrorism and their financing, and improving the efficiency and guarantees of criminal procedure” in 2015, mentioned above.
At the same time, it should be noted that the links between voice analysis and justice are multiplying: there are new specialized agents to support investigators. For example, the company Agnitio, whose Batvox software is used by several police departments in Europe, was able to authenticate the voice of Jérôme Cahuzac in the recordings revealed by Mediapart in 2013 and reused by the courts. Moreover, this episode had raised reactions in the scientific community on the reliability of the use of such devices in judicial proceedings: “Despite the constant progress of Science, researchers in the field consider almost unanimously that current methods of voice recognition are unclear,” according to J.-F. Bonastre, professor at the Computer Science Laboratory of Avignon and specialist in speech processing and voice authentication (whose interview given at the LINC in 2017 can be found here). He also reminds us in an article entitled “1990-2020: retrospectives on 30 years of exchanges around voice identification in forensic environments” that the scientific fundamentals of voice expertise are contested by academic researchers, and that a position of the francophone scientific community on the subject has not changed since a motion was voted in 1990. It is interesting to note that researchers participating in trials do so under the label of scientific witnesses and not judicial experts.
View the full article here !
Our voice is unique.
However, with digital technology’s advent and the proliferation of technologies such as DEEPFAKE AUDIO, the voice can now be synthesized, modified, andrecognized.
Unfortunately, nowadays, one of the necessary means of witness protection used in all news reports and criminal cases remains the voice modification by linear effects existing on the market, such as the “pitch” effect: a transformation of the tone of a processed signal.
These working methods date back to the analog era. Today, simple inverse functions are available on the internet. That research access to a signal’s spectral representation, the equivalent of a voice fingerprint, reverse all existing audio effects.
These methods have become obsolete and dangerous and do not guarantee the anonymity of witnesses.
A protection flaw that few official services, especially the Justice, seem to know.
In concrete terms, if we take an example of spectral representation, the analysis before and after the pitch does not modify the fundamentals of the signal.
No modification is observed. This confirms the NON-PROTECTION of the voice of the witnesses by simple treatment of “pitch” or other linear effects.
Based on this observation, which we are not the only ones to denounce*, after four years of research and development with specialized researchers and the support of RIAM, CNC, BPI, and INRIA, SWEALINK offers the only secure protection for the voice of witnesses, a plug-in under the name VOX PROTECT.
As proof of its irreversibility, if we compare the original voice and the voice processed by VOX PROTECT, we can see that the signal has indeed undergone essential transformations, thus protecting the witness from a voice recognition by the analogy of signals.
VOX PROTECT is the only software that protects the witness, the plug-in user, and the software itself by its innovative operating model.
*For more information: www.voxprotect.com
To receive the press kit: contact@voxprotect.com

Our voice is unique.
However, with digital technology’s advent and the proliferation of technologies such as DEEPFAKE AUDIO, the voice can now be synthesized, modified, andrecognized.
Unfortunately, nowadays, one of the necessary means of witness protection used in all news reports and criminal cases remains the voice modification by linear effects existing on the market, such as the “pitch” effect: a transformation of the tone of a processed signal.
These working methods date back to the analog era. Today, simple inverse functions are available on the internet. That research access to a signal’s spectral representation, the equivalent of a voice fingerprint, reverse all existing audio effects.
These methods have become obsolete and dangerous and do not guarantee the anonymity of witnesses.
A protection flaw that few official services, especially the Justice, seem to know.
In concrete terms, if we take an example of spectral representation, the analysis before and after the pitch does not modify the fundamentals of the signal.
Spectral representation of the original voice:

Spectral representation of the “pitched” voice:
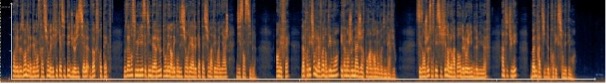
No modification is observed. This confirms the NON-PROTECTION of the voice of the witnesses by simple treatment of “pitch” or other linear effects.
Based on this observation, which we are not the only ones to denounce*, after four years of research and development with specialized researchers and the support of RIAM, CNC, BPI, and INRIA, SWEALINK offers the only secure protection for the voice of witnesses, a plug-in under the name VOX PROTECT.
As proof of its irreversibility, if we compare the original voice and the voice processed by VOX PROTECT, we can see that the signal has indeed undergone essential transformations, thus protecting the witness from a voice recognition by the analogy of signals.
Original voice:

Voice processed by the VOX PROTECT software:
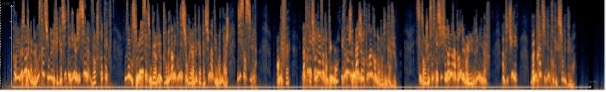
VOX PROTECT is the only software that protects the witness, the plug-in user, and the software itself by its innovative operating model.
*For more information: www.voxprotect.com
To receive the press kit: contact@voxprotect.com











